Cisco FirePOWER DNS Security Intelligence Policy v6
DNS-based Security Intelligence allows you to use your FirePOWER implementation to blacklist traffic based on the domain name lookup requested by a client workstation.
What’s cool is that items configured here are blocked BEFORE access control rules so you can block bad traffic without wasting resources inspection it further based on the work Cisco has already done, and continues to do via the Cisco Talos Security Intelligence and Research Group. These lists we’ll select below are automatically updated as Cisco locates new threats.
This document assumes you already have your FirePOWER implementation working and configured (version 6.0 minimum), if you don’t check out this article:
Cisco FirePOWER Management Center v6 Initial Installation
This document also assumes you want to use Cisco’s pre-configured and automatically updated domain name intelligence lists.
Initial Configuration
- Navigate to Policies > Access Control and edit your Access Control Policy
- Click on the Security Intelligence tab
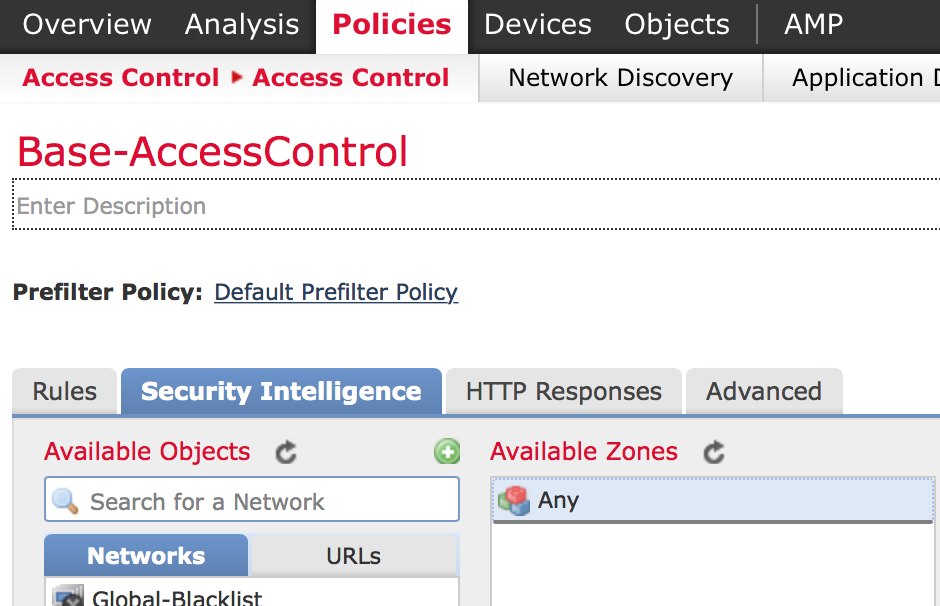
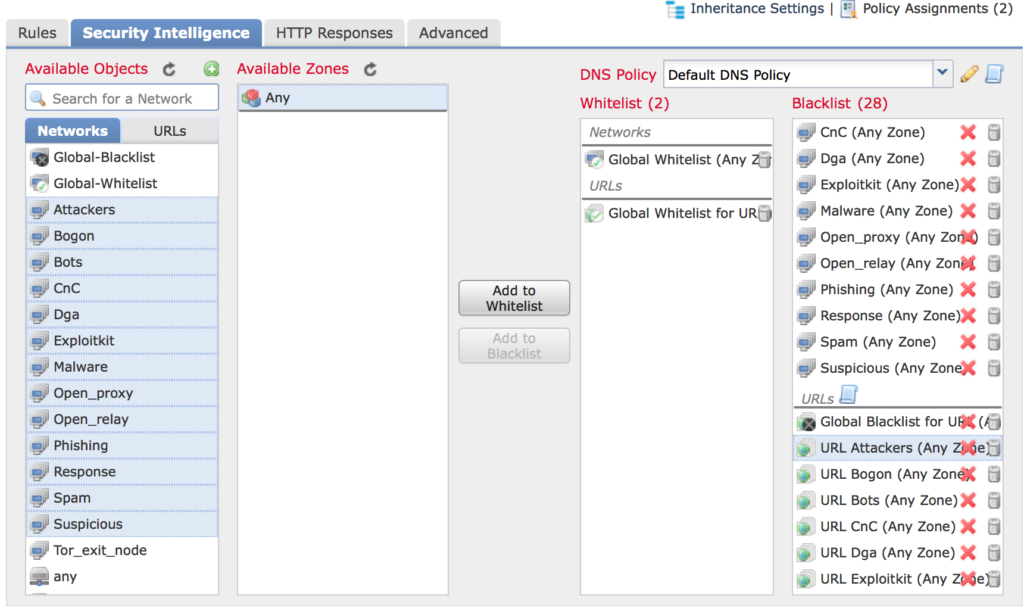
- Highlight the networks you want to block and click Add to Blacklist.
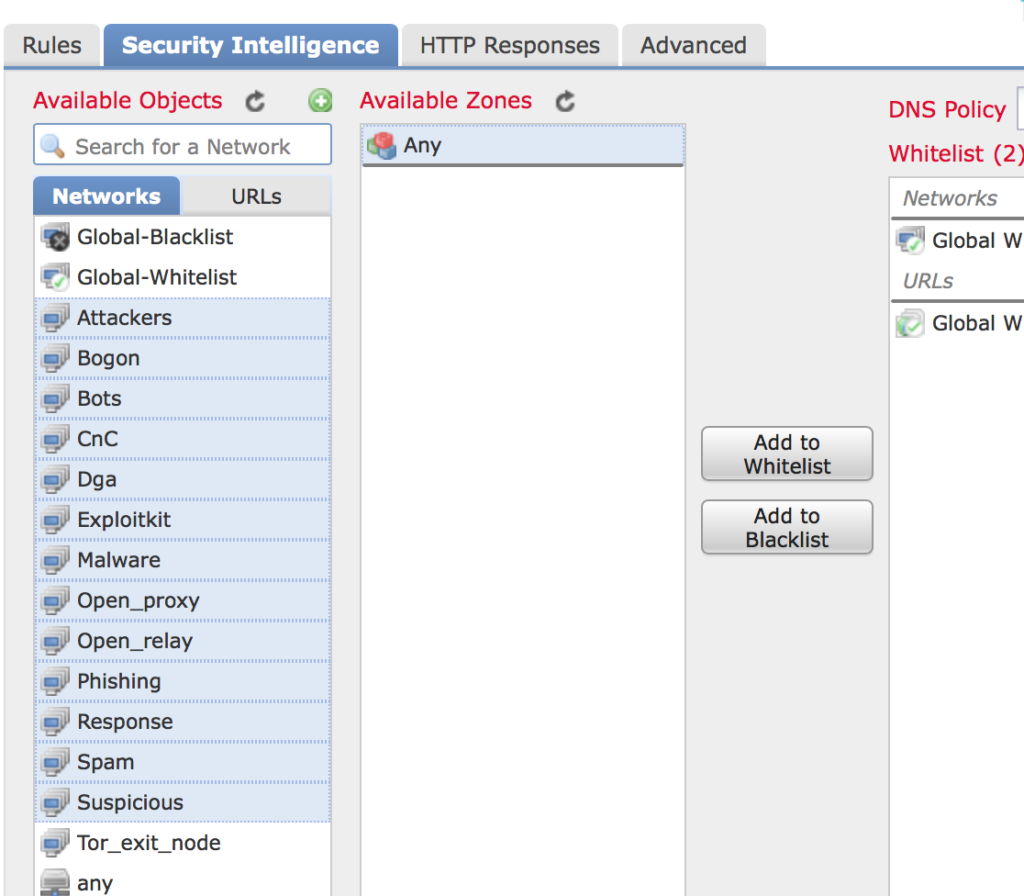
- Click URLs and highlight the Cisco maintained groups you want to block and click Add to Blacklist.
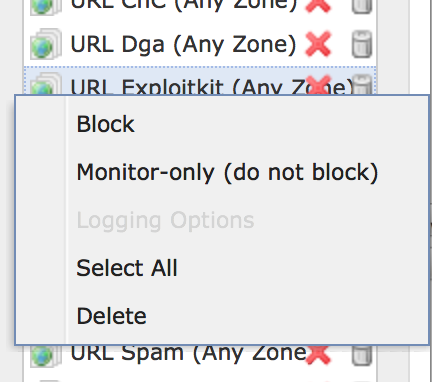
- The default setting is block when you add them to the blacklist. Right click on any of the categories you would prefer to not block, but gather intelligence on and choose Monitor.
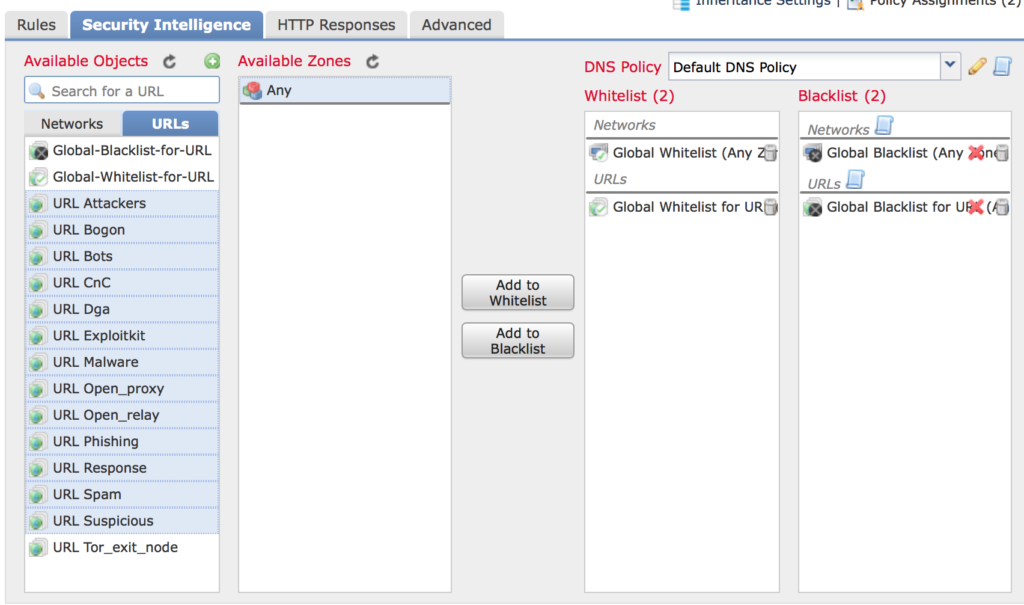
- Here’s what my policy looks like before I click Save. I’ve highlighted what I’m blocking which is all but Tor_exit_node
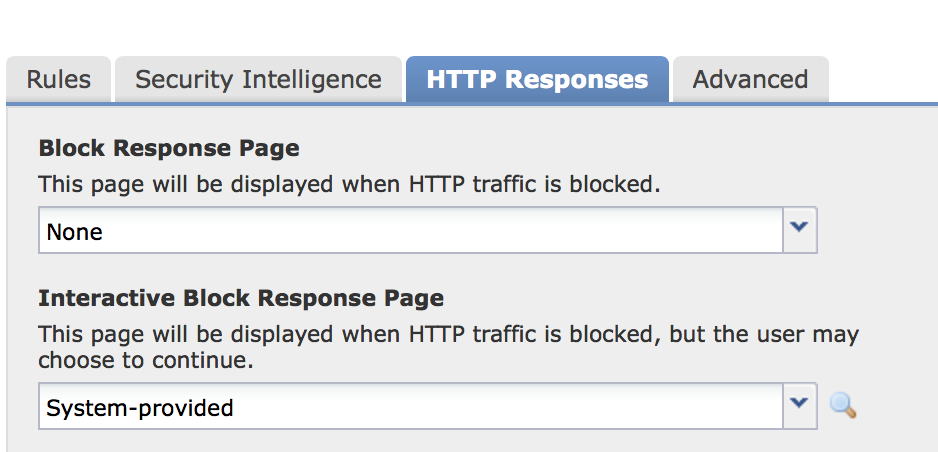
- If you click on the HTTP Responses tab you can set what is provided when a page is blocked. The default is to provide nothing, so the page just errors out instead of loading. Alternatively you can change it to system provided or create your own page.
- Click Save and Deploy to load up the new settings.
Review Policy Hits
After your new changes have been deployed you can check and see what’s hitting and what’s not.
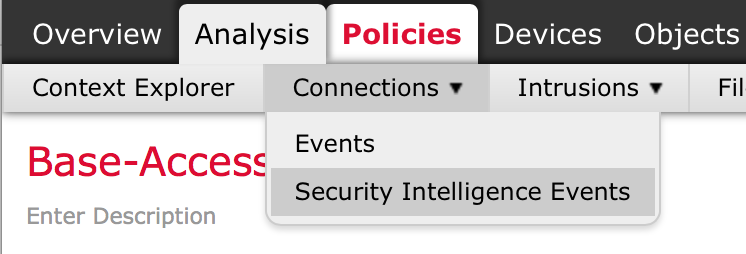
- Navigate to Analysis > Connections > Security Intelligence Events
I’ll be doing more detailed write-ups on both dashboards and Analysis in the future.