Cisco Group Encrypted Transport VPN (GETVPN)
GETVPN is Cisco’s implementation of the GDOI standard (Group Domain of Interpretation). GDOI was originally created to allow for a less-cumbersome way to encrypt multicast traffic, an alternative to GRE over IPSEC tunnels.
These days, GETVPN is used for private networks like MPLS where you use a single Security Association for all routers in a group. It gets around traditional IPSEC’s scaling issue (IPSEC being point to point) by issuing a single IPSEC SA for all routers in the group.
GETVPN has four main components:
- Group Member (GM)
- Key Server (KS)
- Group Domain of Interpretation (GDOI)
- IPSEC
Group Member
The GM is a VPN router that is a member of the group and encrypts traffic with the other GMs. All GMs have the same IPSEC SA, so any GM can encrypt traffic with any other GM (scalable)
Key Server
The KS handles group registration and authentication of GMs. Each GM that needs to join the group will register with the KS to obtain encryption keys and the overall policy for the network.
The registration process checks a group ID and the IKE credentials. Assuming these check out during registration, the Key Server sends the security policy the group is using and two keys KEK (Key Encryption Key) for rekey messages and TEK (Traffic Encryption Key), the primary IPSEC SA used to encrypt traffic between devices.
One important distinction, the KS is NOT a GM, it doesn’t become part of the group, it doesn’t install or use the IPSEC SA.
GDOI
This is the protocol used between the KS and the GMs. It’s protected with ISAKMP phase 1 (just like a normal VPN). All of the standard options (like preshared key or certificates) are supported.
IPSEC
ESP (Encapsulation Security Payload) is used, just like traditional VPNs. Only tunnel mode is supported but the difference here is that GETVPN uses tunnel mode with address preservation, meaning it copies the inner IP header to the outer IP header, without any changes!
Example: We’ll use 3 routers, R1 is the key server, R2 and R3 will be the Group Members. We will use EIGRP for the routing.
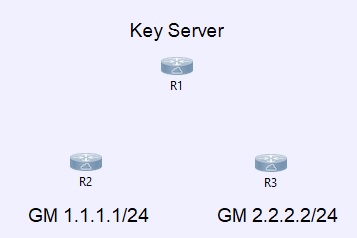
First we setup the Key Server, R1
!generate the crypto key
crypto key generate rsa modulus 1024 label ciscor1
!
!configure phase 1 (isakmp policy)
crypto isakmp policy 10
encr 3des
group 2
authentication pre-share
!
!configure phase 2 (ipsec transform set)
crypto ipsec transform-set TS esp-aes-256 esp-sha-hmac
!
!configure interesting traffic ACL
ip access-list extended GMACL
permit 1.1.1.1 0.0.0.255 2.2.2.2 0.0.0.255
permit 2.2.2.2 0.0.0.255 1.1.1.1 0.0.0.255
!
!configure the keyring
crypto keyring TEST
pre-shared-key address 0.0.0.0 0.0.0.0 key cisco
!
!configure ipsec profiles
crypto ipsec profile GM_Prof
set transform-set TS
!
!Configure GDOI server groups
crypto gdoi group GM
idenity number 1234
server local
rekey authentication mypubkey rsa ciscor1
rekey algorithm aes 256
rekey lifetime seconds 300
rekey retransmit 10 number 3
rekey transport unicast
sa ipsec 10
profile GM_Prof
match address ipv4 GMACL
exit
address ipv4 (address of interface)
Next up is the first Group Member, R2
!generate the crypto key
crypto key generate rsa modulus 1024 label ciscor2
!
!configure phase 1 (isakmp policy)
crypto isakmp policy 10
encr 3des
group 2
authentication pre-share
!
!configure the keyring
crypto keyring TEST
pre-shared-key address 0.0.0.0 0.0.0.0 key cisco
!
!configure GDOI groups
crypto gdoi group GM
identity number 2341
server address ipv4 (KS address)
client registration interface gi2
!
!crypto map setting GDOI groups
crypto map S2S
set group GM
!
!bind crypto map to interface and add EIGRP authentication
int gi2
ip authentication mode eigrp 10 md5
ip authentication key-chain eigrp 10 cisco
crypto map S2S
!
!Configure key chain
key chain cisco
key 1
key-string cisco
!
!Routing (using EIGRP for this example)
router eigrp 10
addres-family ipv4 autonomous-system 10
network x.x.x.x 0.0.0.255
no auto-summary
exit-address-family
!
For Group Member R3 it’s the same as above but replace the appropriate IP’s.